A new report from blockchain analysis firm Chainalysis found that crypto related crimes decreased in 2023. While notable, findings also show that ransomware and darknet market activity involving cryptocurrency increased considerably.
Eric Jardine, cybercrime research lead for Chainalysis, told Cryptonews that both ransomware wallets and darknet market wallets saw more inflows during 2023 than 2022 measured in terms of dollars. Jardine further explained that these two categories of illicit activity involve different underlying patterns of behavior. He said:
“In the case of ransomware, for example, increased inflows mean that individuals, companies, critical infrastructure providers, and governments are paying more or larger ransoms after being the victim of a cyberattack by a malicious actor in 2023 than they did in 2022. In the case of darknet markets, inflows often represent various forms of illegal activity, most notably the purchase of illicit drugs such as fentanyl, heroin, or cocaine.”
Why ransomware and darknet market activities are increasing
Unfortunately, Jardine believes that 2023 marked the recovery of the illicit darknet ecosystem. He mentioned that the closure of Hydra Marketplace in 2022 – one of the largest darknet marketplaces – reduced the aggregate inflows to darknet markets that year. However, this also resulted in an influx in darknet market activity during 2023.
A blog post from Financial Crime Academy notes that darknet marketplaces often use cryptocurrency to facilitate payments due to their anonymous nature. This may be the case, as there is a long standing history behind crypto and darknet marketplaces.
For instance, The Silk Road was an online darknet market that was known for using Bitcoin (BTC) to conduct money laundering activities and illegal drug transactions. The Silk Road was shut down in 2013 by The Federal Bureau of Investigation (FBI). Another darknet marketplace known as Abraxas was closed in 2015, yet it was reported that in 2023 an entity moved 4,800 BTC – worth $144 million at the time – to a coin mixer from a wallet tied to Abraxas.
Ransomware attacks involving cryptocurrency also increased last year. According to a report from the bug bounty platform Immunefi, ransomware attacks use ransomware, which is a form of malware designed to encrypt files on a device or entire network and make them inaccessible. Ransomware groups carry out these attacks and then demand a ransom in return for returning control of those systems. The report further pointed out that the top 10 crypto ransomware attacks since 2020 have profited $69,316,140 in Bitcoin.
Nir Duan, chief executive officer of Sayfer – a blockchain cybersecurity company – told Cryptonews that this is primarily due to a surge in malware-as-a-service (MaaS). He said:
“Today, you don’t need to be a developer or coder to hack a system, as these services can be bought. You can simply purchase the infrastructure, send an organization’s employees a phishing email, and hope for a slip-up that grants you access. The only responsibility left for a bad actor is the negotiation.”
According to Duan, an example of this could involve phishing-as-a-service infrastructure. “This service allows individuals to purchase a counterfeit website that imitates a legitimate cryptocurrency exchange. The individual then entices people to deposit money using various tactics, such as pig butchering or romance scams, before disappearing with the funds,” he said.
In particular, pig butchering schemes involving cryptocurrency have been increasing. In April 2023, the U.S. Department of Justice announced it had seized cryptocurrency worth an estimated $112 million linked to pig butchering. On Jan. 19, The Commodity Futures Trading Commission (CFTC) charged digital asset platform Debiex for engaging in pig butchering, resulting in the loss of $2.3 million from investors.
In addition, “crypto drainer” malware is being used more frequently. A recent report from cybersecurity company Group-IB explains the case of the Inferno Drainer, which is a phishing operation that functions under the “scam-as-a-service” model. According to Group-IB’s findings, the Inferno Drainer was a multichain crypto drainer that was active between Nov. 2022 until Nov. 2023. Last year, the Inferno Drainer malware compromised about 130,000 victims and stole close to $87 million worth of digital assets.
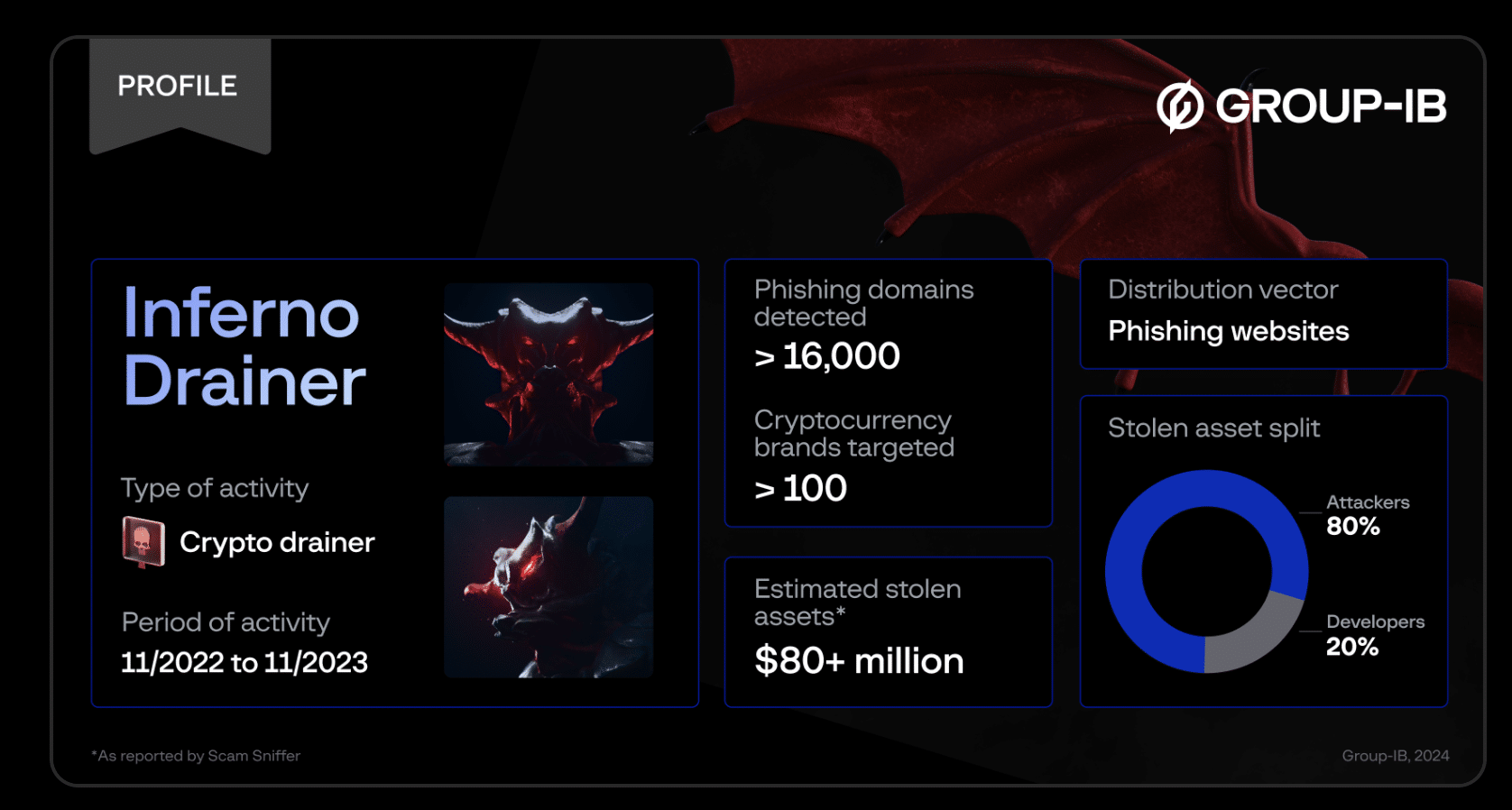
The report mentions that The Inferno Drainer would lure in potential victims with phishing sites that impersonated crypto brands. The cybercriminals also spoofed popular Web3 protocols such as Seaport, WalletConnect, and Coinbase to initiate fraudulent transactions. Rustam Mirkasymov, head of threat intelligence at Group-IB (EU Region), told Cryptonews that in the case of an attack on a crypto service provider, the asset owners themselves cannot influence the security of their funds since they have entrusted these to the service provider.
Combating illicit activities
Although ransomware and darknet activities are increasing, it’s important to point out that solutions are being implemented to combat these crimes.
For instance, The Darknet Marketplace and Digital Currency Crimes Task Force was created in June last year to target “cryptocurrency-enabled crimes” such as drug trafficking, money laundering, theft of personal information and child exploitation. Jardine pointed out that there is indeed a role for law enforcement in attempting to find and arrest perpetrators. “Undertaking this sort of enforcement action is made easier by the traceability of blockchains,” he said.
Jardin added that individuals, businesses, critical infrastructure providers and governments must also be proactive in protecting their computer networks and information technology systems from ransomware attacks. “Creating a safer and more trustworthy on-chain environment requires action by various public and private sector actors as well as individuals themselves.”
While best practices are important to consider, Duan shared that Sayfer is developing an on-chain-off-chain investigation tool, which serves as a proactive defense against malware techniques. “Instead of focusing on individual actors, our tool detects the underlying infrastructure used. We believe this approach will make us more effective and efficient in combating the rise of these illegal activities, he said. According to Duan, Sayfer has encountered the same infrastructure used for 10 unrelated phishing scams within the last year. “Some of these scams targeted the Asian market, others the U.S. market, but all employed the same phishing infrastructure.”
Unfortunately, Duan believes that ransomware and darknet market crimes using cryptocurrency will continue to increase moving forward. This is due to the rise of franchising specific malware tools coupled with evolving technology. “By selling the infrastructure and allowing anyone to use it, bad actors are facilitating the increase in criminal activity. Secondly, the technology and methods are still in their early stages of development and will continue to evolve, leading to more advanced systems,” he said.
Echoing this, Jardin believes that illicit activity on-chain is likely to continue to increase as the use of cryptocurrency grows over time. Yet he noted that enforcement actions are gaining traction in frequency and sophistication. “I would expect these actions to continue to help clamp down on the worst possible outcomes going forward.”
