Cyber security experts at ESET have warned firms of the threat posed by the Lazarus Group’s new malware “LightlessCan” saying it is more difficult to detect than previous versions.
According to the firm, the malware is mostly deployed in employment scams luring users to install a malicious payload disguised as a job task or document related to the company.
In its recent blog post on Sept 29, the firm highlighted how the new malware works, its damage to the network systems, different execution chains leading to cyber espionage, etc.
The Lazarus Group has been linked to several crypto hacks running into millions of dollars most notably the incident which saw over $40 million wiped from sports betting platform, Stake.com.
The group was also linked to the Bitthumb, Nicehash incidents which recorded millions stolen alongside hacks on traditional companies like AstraZeneca, Sony, WannaCry, etc.
Here’s how it worked
The cyber security experts explained that the hackers deliver payloads to the victim’s network by utilizing a remote access Trojan, a far more sophisticated advancement than previous versions.
“LightlessCan mimics the functionalities of a wide range of native Windows commands, enabling discreet execution within the RAT itself instead of noisy console executions. This strategic shift enhances stealthiness, making detecting and analyzing the attacker’s activities more challenging.”
LightlessCan also uses guardrails which serve as protective mechanisms for the payload during its execution, “effectively preventing unauthorized decryption on unintended machines, such as those of security researchers,” they added.
Per the report, after initial access was gained through a social media hiring process, it used multiple encryptions, AES-128 and RC6 with a 256-bit key from its previous campaigns like the Amazon incident.
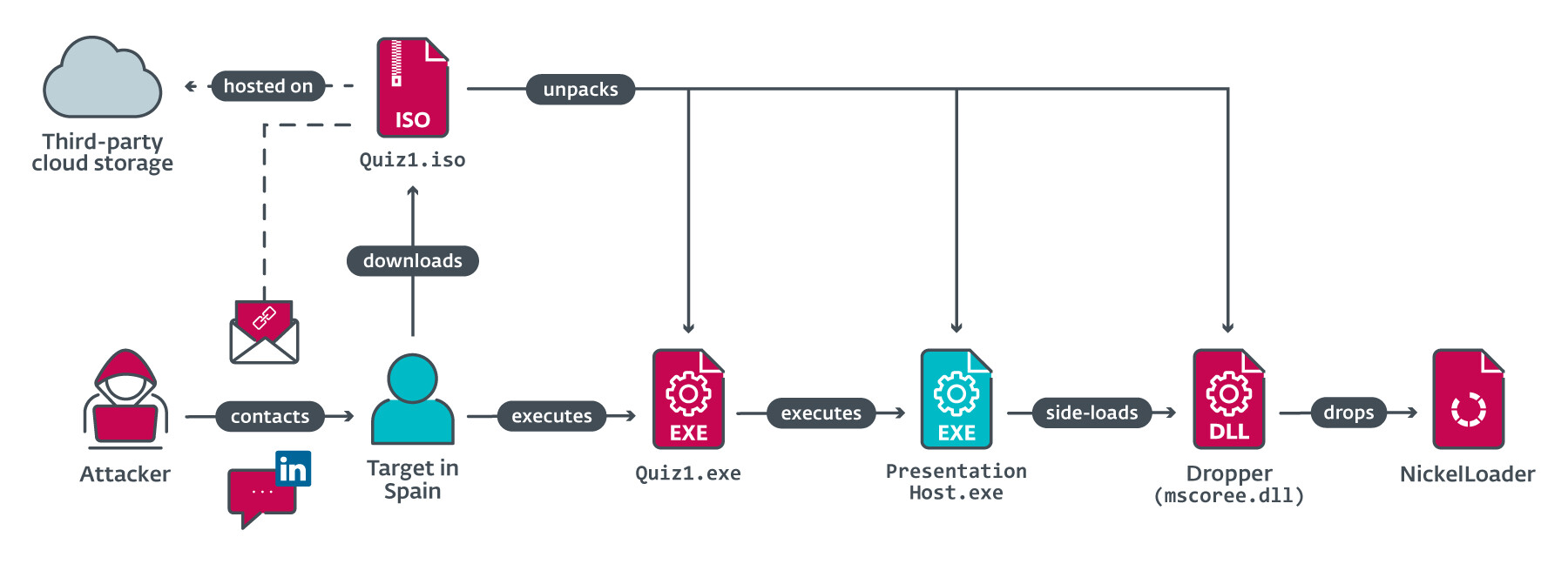 The RATs deployment in the final stages work with droppers and loaders that are embedded with payload into the systems
The RATs deployment in the final stages work with droppers and loaders that are embedded with payload into the systems
“The most interesting payload used in this campaign is LightlessCan, a successor of the group’s flagship HTTP(S) Lazarus RAT named BlindingCan. LightlessCan is a new complex RAT that has support for up to 68 distinct commands, indexed in a custom function table, but in the current version, 1.0, only 43 of those commands are implemented with some functionality.”
Finally, the security team called for renewed awareness of related scams to drastically reduce their occurrence to achieve digital safety.
Spain’s aerospace company as a case study
The firm uncovered a hack by the Lazarus Group on a Spanish aerospace company leveraging the new LightlessCan model.
The bad actors gained access to the company’s networks last year after a series of targeted campaigns acting as a recruiter for the company.
They contacted the victim through Linkedin and sent two coding tasks as part of the hiring strategy. The first task was a basic display of “Hello, World!” while the second involved printing of a Fibonacci sequence.
Cyber security experts at ESET have warned firms of the threat posed by the Lazarus Group’s new malware “LightlessCan” saying it is more difficult to detect than previous versions.
According to the firm, the malware is mostly deployed in employment scams luring users to install a malicious payload disguised as a job task or document related to the company.
In its recent blog post on Sept 29, the firm highlighted how the new malware works, its damage to the network systems, different execution chains leading to cyber espionage, etc.
The Lazarus Group has been linked to several crypto hacks running into millions of dollars most notably the incident which saw over $40 million wiped from sports betting platform, Stake.com.
The group was also linked to the Bitthumb, Nicehash incidents which recorded millions stolen alongside hacks on traditional companies like AstraZeneca, Sony, WannaCry, etc.
Here’s how it worked
The cyber security experts explained that the hackers deliver payloads to the victim’s network by utilizing a remote access Trojan, a far more sophisticated advancement than previous versions.
“LightlessCan mimics the functionalities of a wide range of native Windows commands, enabling discreet execution within the RAT itself instead of noisy console executions. This strategic shift enhances stealthiness, making detecting and analyzing the attacker’s activities more challenging.”
LightlessCan also uses guardrails which serve as protective mechanisms for the payload during its execution, “effectively preventing unauthorized decryption on unintended machines, such as those of security researchers,” they added.
Per the report, after initial access was gained through a social media hiring process, it used multiple encryptions, AES-128 and RC6 with a 256-bit key from its previous campaigns like the Amazon incident.
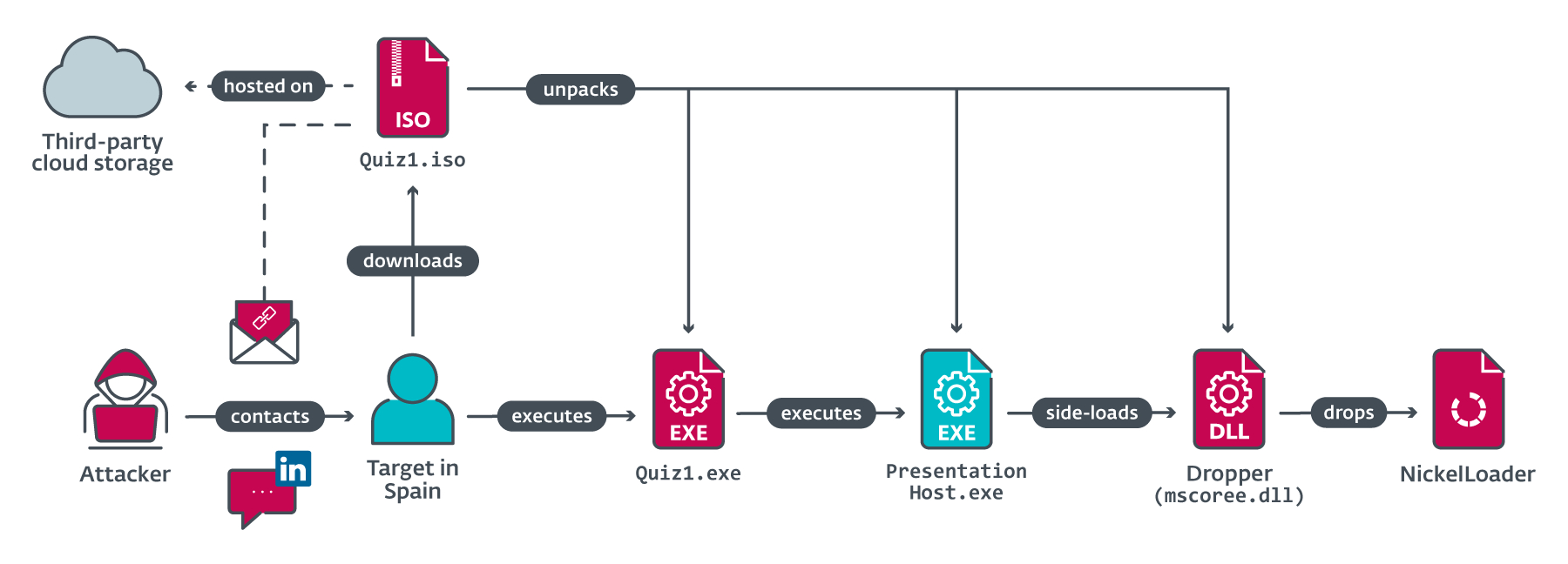 The RATs deployment in the final stages work with droppers and loaders that are embedded with payload into the systems
The RATs deployment in the final stages work with droppers and loaders that are embedded with payload into the systems
“The most interesting payload used in this campaign is LightlessCan, a successor of the group’s flagship HTTP(S) Lazarus RAT named BlindingCan. LightlessCan is a new complex RAT that has support for up to 68 distinct commands, indexed in a custom function table, but in the current version, 1.0, only 43 of those commands are implemented with some functionality.”
Finally, the security team called for renewed awareness of related scams to drastically reduce their occurrence to achieve digital safety.
Spain’s aerospace company as a case study
The firm uncovered a hack by the Lazarus Group on a Spanish aerospace company leveraging the new LightlessCan model.
The bad actors gained access to the company’s networks last year after a series of targeted campaigns acting as a recruiter for the company.
They contacted the victim through Linkedin and sent two coding tasks as part of the hiring strategy. The first task was a basic display of “Hello, World!” while the second involved printing of a Fibonacci sequence.
